Top Five Stupid Ways Spammers Shoot Themselves in the Foot
Spammers invest a great deal of time and money in the business of bothering of other people. They rent e-mail lists from other spammers, pay for spam templates, and face other costs.
While spammers collectively cost businesses billions of dollars per year in lost productivity, they do actually have to outlay some cash for it.
And that’s all the more reason for the honest citizens of the world to feel a little victorious when spammers foil their own plans by forgetting to include attachments, getting company names mixed up, or any of the other Top Five Stupid Ways Spammers Shoot Themselves in the Foot.
Old-school spammers have learned that the success of a campaign lies in getting the tiniest details straight. Many of the “n00bs” haven’t spammers who buy anything, from victim lists to templates, sometimes shoot themselves in the foot in the process. Here are some of the worst mistakes newbie-spammers make to ruin their own nefarious plans.
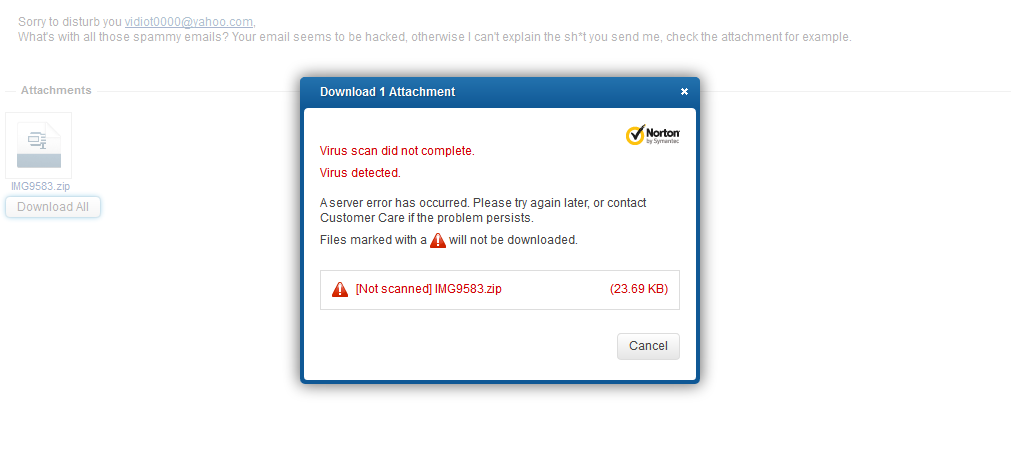
1.Sending infected attachments that can’t be opened
Infected attachments are still the favorite means of compromising a user’s computer. Be they executable files, archives with executable files or exploit-laden documents, these files pose a real threat to computer users and some free webmail services have implemented scanning technologies on the mail servers. Here is what happens when spammers send infected files to these services:

2.Using IPs instead of domains in spam campaigns
Spammy domains have an average time of 2-3 days at most before they get blacklisted by security companies or by organizations that provide browsers with blacklists.
That is why cyber-criminals sometimes use hard-coded IPs in URLs rather than domain names. However, these IPs are usually blacklisted from other spam campaigns, which automatically voids the campaign.
3.The empty message
“More haste, less speed,” goes the old proverb. This applies especially when you’re delivering a “promotional” message to millions of potential “customers.” Many times, spammers craft their message in a hurry, and often mess up HTML code, as in the image below. The addition of a simple character (<€) would prevent the rest of the text from displaying, as the e-mail client treats it as a HTML tag.
This would be a totally wasted campaign, as, even if spam filters wouldn’t detect it, the attackers would not be able to get their message through to the victim.
4.Who did you say you were working for?
Spammers like to re-use templates. They gain extra time – and we all know time is money. Sometimes, though, they forget what the scam was about, and the attack becomes improbable even for the weakest target.
LinkedIn notification scam re-used for financial fraud. A big inconsistency that destroys a spam campaign.
5.The attachment – Where is the attachment?
Other times, spammers get everything straight: their identity looks bulletproof, the spam template has the right visual cues in place, their message is also crafted as it should. What’s missing is the payload: they forget to add the malicious attachment.
tags
Author

Bogdan is living his second childhood at Bitdefender as director of threat research.
View all postsRight now Top posts
Start Cyber Resilience and Don’t Be an April Fool This Spring and Beyond
April 01, 2024
Spam trends of the week: Cybercrooks phish for QuickBooks, American Express and banking accounts
November 28, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













