Whistler Bootkit Flies Under the Radar
Whistler, one of the first e-threats that could be classified as bootkits, has evolved new means to bypass the AV detection. Bitdefender researcher Mircea Pavel explains:
In the last few months we have spotted a new and widespread MBR infection that we currently classify as Rootkit.MBR.Whistler.B. The new functions have helped it “fly under the radar” so far, so it is being detected by very few AV products other than Bitdefender.
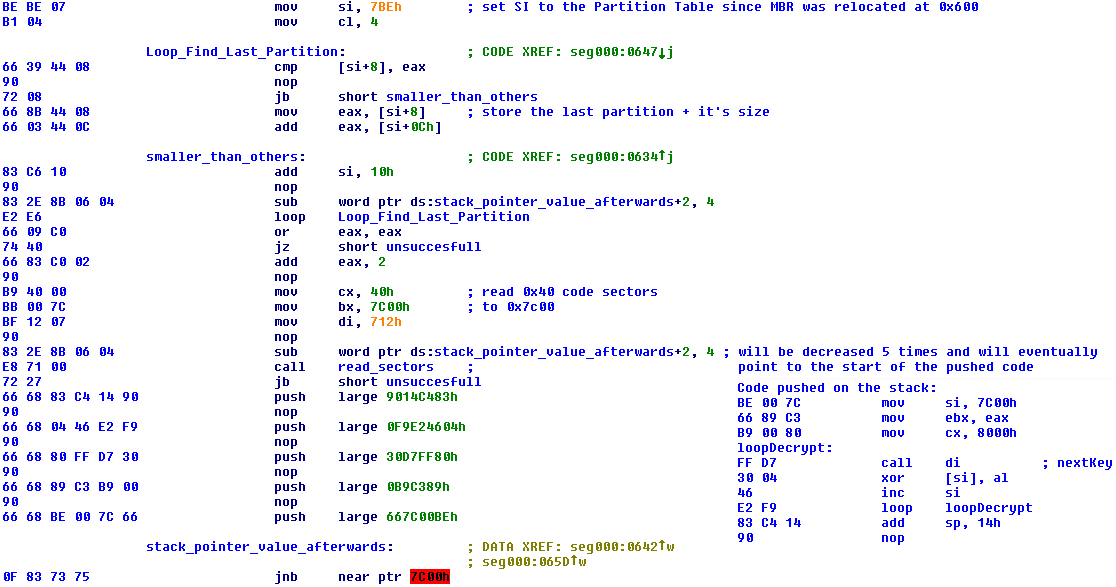
Whistler builds on the stack code that will load the malware code, decrypt it and transfer control to it:
The Whistler bootkit keeps all of its data after the last partition on disk. If there is not enough unpartitioned space, it will shrink the last partition, making sure at least 400 sectors are available. The first sector written after the last partition defines each of the bootkit components along with its type (a 32 byte string that is usually a MD5), size (in bytes) and location (offset starting from the end of the last partition, in sectors). If one sector is not enough to define all components, then an additional structure will be defined and referenced by the first one. First sector, original mbr entry is highlighted, and can be located in this case at sector 0x42
One major change that occurred in newer versions is the complete encryption of Whistler’s data. Since in the early versions only the malicious code was encrypted, the original MBR and other components being left as plaintext in the unpartitioned space, security solutions were able to find the infection easily. In the newer, stealthier variants, components are encrypted, using the LBA of the absolute sector where they are located as a key. This also prevents dumping the sectors from an infected system to reproduce the same infection on another one. The first sector is encrypted differently, based on one additional key that is specific to the system and is hard coded in the malicious code.
Payload is injected in the usermode processes by a driver loaded at boot and is designed to download and execute other files. Once the dropper writes the MBR and the data sectors, it will delete itself. Because of this, even if the infection is spotted, the source of infection is already gone, making its analysis impossible.
Whistler is one of the threats that knows how to stay away from unwanted attention. We investigated systems infected with Whistler and we found it doesn’t hide the MBR code, as other boot-kits do. This makes it less suspicious and gives it more chances to stay in the wild without getting caught by AV products.
Also the payload is quite inconspicuous and doesn’t alert the user, while the bootkit avoids keeping any files on the victim’s disk, writing the code directly in memory where it is harder to be detected. It is almost certain that this bootkit will continue its evolution, improving and adding new components. It was built to be just a layer under which other malware are stealthy loaded so it is possible it would gain more diverse payloads in the near future, hosting different kinds of malware.
Bitdefender currently cleans Whistler infections, restoring the clean MBR and removing all the remaining virus data that might represent a threat for the user.
tags
Author

Razvan Stoica is a journalist turned teacher turned publicist and technology evangelist. Recruited by Bitdefender in 2004 to add zest to the company's online presence.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks
















