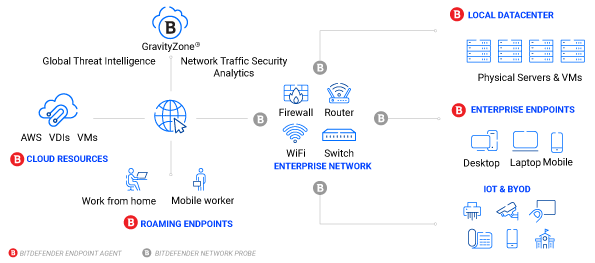
Bitdefender technology is built to detect and respond to host-based threats by analyzing the network traffic. It uses machine learning and heuristics to analyze behavior in real-time to accurately uncover malware activities like lateral movements and brute force attempts. This improves the visibility and control of host-based network threats.

Initial access techniques use various entry vectors to gain their foothold within a network. Techniques include targeted spearphishing and exploiting weaknesses on public-facing web servers.
Network attack defense hardens protocols like HTTP, SMB, RPC and analyzes network traffic to block attacks like SQL injection, brute force and drive-By downloads

Network attack defense prevents exfiltration and secures sensitive information by cybercriminals who use techniques like keylogging or credential dumping for stealing account names and passwords.

Cybercriminals use discovery techniques to gain knowledge about the internal network. They scout for weaknesses and orient themselves before deciding which assets to compromise.
Native operating system tools are often used toward this post-compromise information-gathering technique. Bitdefender network protection can quickly spot and halt these discovery attempts

Cybercriminals move laterally to invade and control remote systems on a network. Post asset discovery, attackers either look to spread the infection or gain elevated privileges. Adversaries might also install custom tools using legitimate credentials with native network and operating system tools. Our patented technology can harden endpoint defenses by providing an additional layer of security.

Crimeware is not a purely technical threat but more of a socio-technical affair spread for financial gains. Cyber criminals latch onto and steal transactional data like social security numbers, phone numbers, personal addresses, medical records, etc. Bitdefender network protection achieves complete visibility to detect techniques that elude security mechanisms to stop cybercriminals from misusing sensitive information.
A resource-efficient security solution that provides high performance and protection while delivering centralized management, easy deployment, and the freedom to choose between a cloud or an on-premise hosted management console.
Safeguards your organization from sophisticated cyber-attacks like Advanced Persistent Threats (APTs) and ransomware with more than 30 layers of machine-learning-driven security technologies.

